

Chapter 10 Deploying Applications Around Proxies and Firewalls
Reverse proxies typically act as a gateway for incoming connections to an organization's network servers, preventing direct connections from clients outside the firewall to servers inside the firewall. The reverse proxy can enhance security, by restricting protocols and logging connection activity. Reverse proxies may also act as caches to respond to common requests. In some cases, multiple reverse proxies may be deployed to cache results from one server, as a form of load balancing. Figure 10-2 shows how clients connect through a reverse proxy.
Figure 10-2: Connecting through a reverse
proxy
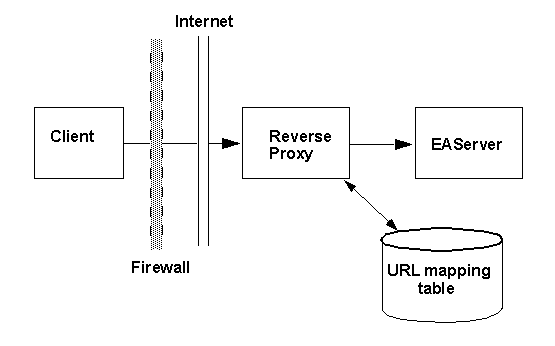
Clients connect to EAServer through a reverse proxy as follows:
GET /host/port/HIOP/1.0/...
For use with EAServer, you must configure your reverse proxy server's URL mapping table to recognize the EAServer addresses embedded in the HTTP requests sent by the client runtime. For each EAServer that clients can connect to through the server, configure a mapping for the following URL prefix:
GET /host/port/HIOP/1.0/
Where host is the target EAServer listener host name, and port is the target EAServer listener port number. For each EAServer that you deploy behind the reverse proxy, add a mapping for each IIOP, IIOPS, and Message Service listener address. If you deploy an EAServer cluster behind a reverse proxy, add mappings for each server in the cluster.
To connect through a reverse-proxy server, you can set the properties in Table 10-2. You must set these properties in addition to any properties that you would set to connect directly to EAServer.
| CORBA property | EJB property | To indicate |
|---|---|---|
| com.sybase.CORBA. ProxyHost |
com.sybase.ejb. ProxyHost |
Specifies the machine name or the IP address of the reverse-proxy server. |
| com.sybase.CORBA. ProxyPort |
com.sybase.ejb. ProxyPort |
Specifies the port number of the reverse-proxy server, typically 80 for HTTP-tunnelled connections or 443 for SSL (HTTPS-tunnelled) connections. |
| com.sybase.CORBA. http |
com.sybase.ejb. http |
Set this property to true if the reverse-proxy server requires HTTP-tunneled connections. If you do not set this property, connections still go through, but only after the client ORB first tries to open an IIOP connection. Setting the property eliminates the overhead that is incurred by trying plain IIOP each time a connection is made. |
| com.sybase.CORBA. forceSSL |
com.sybase.ejb. forceSSL |
Set this property to true if the connection to the reverse proxy must use SSL (HTTPS) tunnelling, but the connection from the proxy to the EAServer does not use SSL tunnelling. |
| com.sybase.CORBA. qop |
com.sybase.ejb. qop |
In Java applications that connect to
a proxy using SSL (HTTPS) tunnelling, set the Quality Of Protection
(QOP) to a security level that matches the level supported by the reverse-proxy
server. For instructions on setting this property, see "SSL
properties". If the connection
to the proxy server requires SSL, but the connection from the proxy
does not, do not set the QOP; instead, set the com.sybase.CORBA.forceSSL property
to true.
Do not set QOP in Java applets that use SSL. Instead, code the applet to connect to a listener that supports the required security level. See "Using SSL in Java applets" for more information. |
| com.sybase.CORBA. autoProxy |
com.sybase.ejb. autoProxy |
In Java applets, set this property to
true to enable connections to a reverse-proxy server. You must also configure
your applet to download through the reverse-proxy server itself.
The default is false. This property is ignored if the client is
not a Java applet, or has not initialized the Java ORB with the ORB.init method
that takes an Applet parameter.
When automatic proxy is enabled, the ORB uses the applet's download address as the reverse-proxy server address. If the port number is 443, SSL (HTTPS tunnelling) is used; otherwise, HTTP tunnelling is used. |
| Copyright © 2002 Sybase, Inc. All rights reserved. |

| |